Zero-Knowledge Proofs for Nepal’s Digital Security & Privacy
1.0 Executive Summary
The Central Argument
Nepal’s rapid and commendable digital transformation, while fostering economic growth and improving service delivery, is concurrently constructing a centralized and increasingly vulnerable information architecture. The current security paradigm, which relies on trusting third-party institutions to safeguard vast repositories of citizen data, is fundamentally misaligned with the escalating sophistication of global cyber threats. This report posits that Zero-Knowledge Proofs (ZKPs), a revolutionary cryptographic technology, offer a necessary paradigm shift. By transitioning from a security model based on “trusted third parties” to one founded on “verifiable cryptographic proof,” ZKPs can directly address and mitigate critical vulnerabilities within Nepal’s foundational digital pillars: national identity, financial services, and e-governance.
Key Findings
The analysis reveals a confluence of systemic risks within Nepal’s digital ecosystem. The nation is grappling with significant data privacy gaps, where constitutional rights to privacy are undermined by a lack of robust enforcement mechanisms and a dedicated data protection authority. The legal framework for cybersecurity, anchored by the outdated Electronic Transaction Act of 2008, is ill-equipped to handle modern cyber threats like ransomware and state-sponsored attacks. This legal deficit is compounded by a severe cybersecurity skills gap, with a projected shortage of thousands of qualified professionals and academic programs that often fail to provide practical, industry-relevant training. This environment of unpreparedness has already led to significant data breaches, exposing the sensitive information of hundreds of thousands of Nepalese citizens.
Core Recommendations
This report identifies and elaborates on three primary, high-impact use cases for the strategic implementation of ZKPs. First, fortifying the National Identity (NID) system by enabling privacy-preserving verification, allowing citizens to prove specific attributes (e.g., age, citizenship) without revealing their entire identity document. Second, enhancing the security and trustworthiness of Nepal’s burgeoning digital finance ecosystem by facilitating confidential credit assessments and regulatory audits. Third, securing sensitive e-governance services, particularly in the realms of verifiable electronic voting and private health information exchange, to bolster both democratic integrity and citizen welfare.
Strategic Imperative
The adoption of Zero-Knowledge Proofs is not merely a technical upgrade; it is a strategic national imperative. In an era where data is a geopolitical asset, implementing ZKPs is essential for safeguarding Nepal’s digital sovereignty. It provides the tools to foster profound citizen trust in digital systems, build a resilient and competitive digital economy, and ensure that the nation’s technological progress does not come at the cost of its citizens’ fundamental right to privacy. This framework presents a clear, actionable path toward achieving that secure and prosperous digital future.
2.0 Demystifying Zero-Knowledge Proofs: A Cryptographic Primer for Strategic Implementation
2.1 The Foundational Concept: Proving Knowledge Without Revealing It
At its core, a Zero-Knowledge Proof (ZKP) is a cryptographic protocol involving two parties: a “prover” and a “verifier”. The objective is for the prover to convince the verifier that a specific statement is true, without conveying any information whatsoever beyond the mere fact of the statement’s truth. The challenge, and the elegance of the solution, lies in proving possession of information without revealing the information itself. This capability is a profound departure from traditional verification methods, which almost invariably require the disclosure of the data being verified.
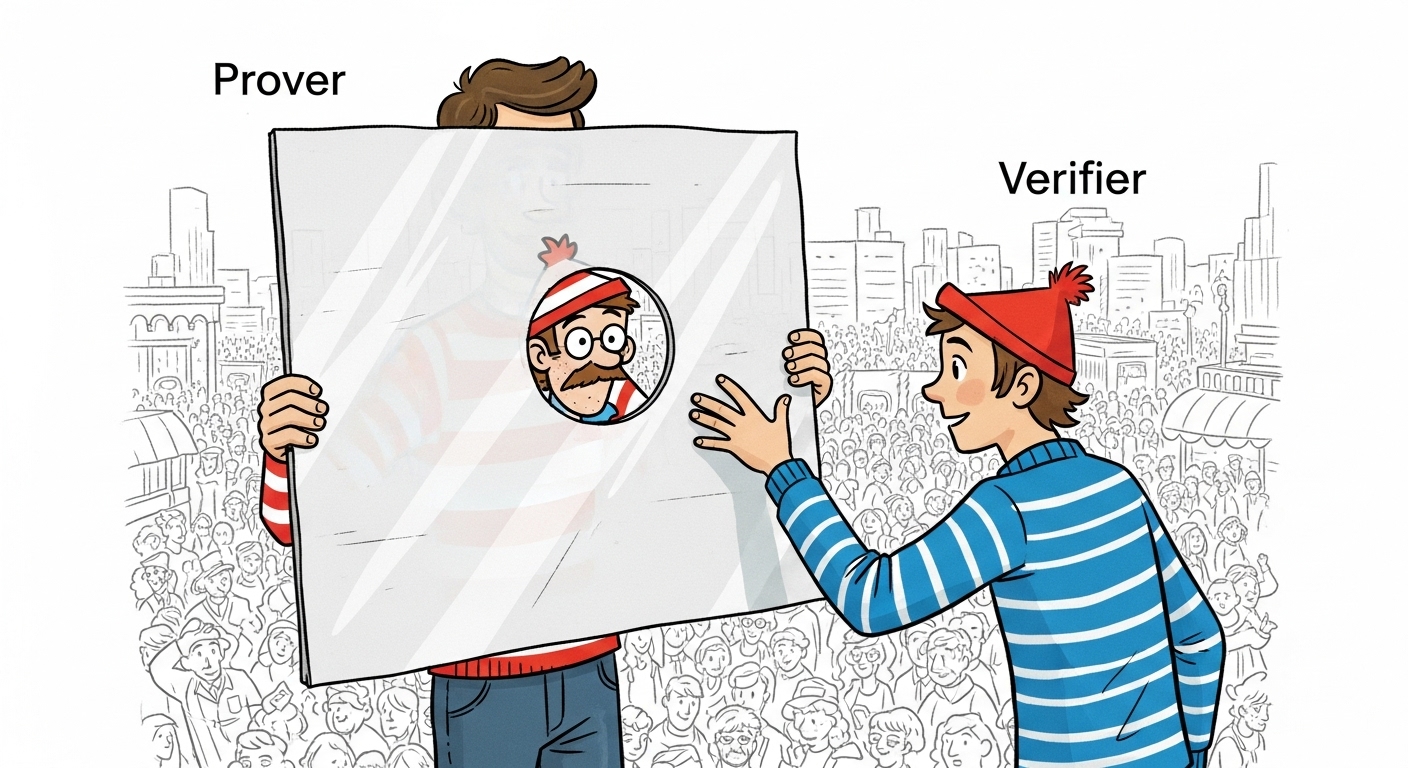
To make this abstract concept more tangible, several analogies are useful for a non-technical audience. One powerful illustration is the “Where’s Waldo?” puzzle. Imagine a prover has found Waldo on a large, complex page and wants to prove this to a skeptical verifier without revealing Waldo’s location. The prover could take a large piece of cardboard, cut a small hole in it just large enough to show Waldo, and place it over the page. The verifier can look through the hole and see Waldo, becoming convinced that the prover knows his location. However, because the rest of the page is obscured, the verifier learns nothing about Waldo’s position relative to other characters or objects on the page. The proof is successfully delivered with “zero knowledge” of the secret location being transferred.
Another classic example is the “red card proof”. A prover (Peggy) claims to hold a red card from a standard deck, but she keeps it face down. To prove her card is red without revealing its suit or rank, she can take the remaining 51 cards and show the verifier (Victor) all 26 black cards. Since Victor knows a standard deck has exactly 26 black cards, and he has seen all of them in the remaining pile, he can conclude with absolute certainty that Peggy’s hidden card must be red. Victor learns only the truth of the statement (“the card is red”) but gains no additional information about the specific card. These examples intuitively capture the essence of ZKPs: verification without disclosure.
2.2 The Three Pillars of Verifiable Trust: Core Principles
For any protocol to be considered a valid Zero-Knowledge Proof, it must rigorously satisfy three fundamental properties. These pillars are what give ZKPs their power and reliability, ensuring they are both secure and functional.
Completeness
The principle of completeness guarantees that if a statement is true, an honest prover will always be able to convince an honest verifier of its truth. This is the property of utility; it ensures that the system works correctly for legitimate users engaged in honest interactions. In the “Where’s Waldo?” example, if the prover genuinely knows Waldo’s location, they can always successfully position the cardboard to convince the verifier. Without completeness, the system would be unreliable and impractical for real-world applications.
Soundness
Soundness is the system’s security guarantee against deception. It ensures that if a statement is false, a dishonest prover cannot convince an honest verifier that it is true, except with a probability so small as to be statistically negligible. This property prevents forgery and fraud. If the prover in the Waldo example did not know his location, they could not reliably place the cardboard to reveal him through the hole; their attempts would fail, and the verifier would not be convinced. Soundness ensures the integrity of the verification process, making the proof a reliable indicator of truth.
Zero-Knowledge
This is the defining, privacy-preserving property of the protocol. If the statement is true, the verifier learns nothing more than the fact that the statement is true. The proof itself reveals no additional information about the secret knowledge held by the prover. This principle directly enables data minimization, a core tenet of modern data protection regulations, by ensuring that only the absolute minimum information required for a transaction (i.e., the proof of a claim’s validity) is ever exchanged. In the red card example, the verifier is convinced the card is red but has no way of knowing if it is the Ace of Hearts or the Two of Diamonds, thus preserving the secrecy of the specific card.
2.3 A Taxonomy of ZKPs: From Interactive Protocols to zk-SNARKs and zk-STARKs
Zero-Knowledge Proofs are not a monolithic technology; they exist in various forms, each with different characteristics, trade-offs, and suitability for specific applications. A strategic understanding of these differences is crucial for policymakers and system architects.
The first major distinction is between interactive and non-interactive proofs. Interactive ZKPs require the prover and verifier to engage in a back-and-forth exchange of messages, or a series of challenges and responses, to complete the proof. While foundational, this interactive nature can be inefficient for systems that need to scale or operate asynchronously, as the prover must be online and available to interact with every verifier.
To address this limitation, cryptographers developed Non-Interactive ZKPs (NIZKs). In a NIZK system, the prover can generate a single, self-contained proof that can be published and then verified by anyone, at any time, without any further interaction with the prover. This “generate once, verify many times” property makes NIZKs far more practical for large-scale applications like blockchain transactions, digital identity verification, and public e-governance systems, where efficiency and scalability are paramount.
Within the family of NIZKs, two types have become particularly dominant: zk-SNARKs and zk-STARKs.
zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge)
are the most widely known and implemented form of NIZK, particularly in the blockchain space. Their key advantages are their “succinctness”—the proofs they generate are extremely small, and they can be verified very quickly. This efficiency makes them highly attractive for applications where storage and computational resources are constrained. However, many zk-SNARK constructions come with a significant caveat: they require a trusted setup. This is a one-time, pre-computation ceremony where cryptographic parameters are generated.
If the secret data used in this ceremony (often called “toxic waste”) is not securely destroyed, it could be used to create false, fraudulent proofs that would appear valid to the system.
zk-STARKs (Zero-Knowledge Scalable Transparent Argument of Knowledge) were developed later to address some of the limitations of zk-SNARKs. Their most important feature is their “transparency”—they do not require a trusted setup, relying instead on publicly verifiable randomness. This eliminates the security risk associated with the setup ceremony. Furthermore, zk-STARKs are built on mathematical foundations that are believed to be resistant to attacks from future quantum computers, making them a more future-proof choice. The primary trade-off is that zk-STARK proofs are significantly larger than zk-SNARK proofs, which can increase storage and transmission costs.
The choice between these technologies is not merely technical but carries deep strategic implications for a sovereign nation. The trusted setup required for many zk-SNARKs represents a potential national security vulnerability. The integrity of a foundational system like a national digital ID depends entirely on the integrity of this initial ceremony. Entrusting this critical process to a single entity, or even a small group, creates a centralized point of failure that could be a prime target for sophisticated state-level adversaries. The compromise of this setup could allow for the forging of identities or credentials on a national scale. In contrast, the transparency of zk-STARKs, which require no such trusted setup, eliminates this entire class of risk. For core national functions such as identity, voting, or central banking, the political and security benefits of transparency and quantum resistance offered by zk-STARKs may therefore far outweigh the performance advantages of zk-SNARKs, despite the latter’s wider current adoption in commercial applications. This is a critical distinction that Nepalese policymakers must weigh when architecting the nation’s future digital infrastructure.
Table 2.1: Comparative Analysis of ZKP Technologies (zk-SNARKs vs. zk-STARKs)
| Feature | zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) | zk-STARKs (Zero-Knowledge Scalable Transparent Argument of Knowledge) |
|---|---|---|
| Trusted Setup | Required for many common constructions. Poses a potential security risk if the setup’s secret data is compromised. | Not required (“Transparent”). Relies on public randomness, eliminating the setup as a single point of failure. |
| Proof Size | Very small (succinct), typically a few hundred bytes. Efficient for on-chain storage and transmission. | Larger, typically in the tens of kilobytes. Can be more costly to store and transmit. |
| Verification Time | Very fast, often constant time regardless of the complexity of the computation being proven. | Fast, but typically slower than zk-SNARKs. Verification time grows poly-logarithmically with computation complexity. |
| Proving Time | Generally faster than zk-STARKs for smaller computations. | Slower for small computations but scales more efficiently for very large and complex computations. |
| Quantum Resistance | Vulnerable to attacks from future quantum computers, as they often rely on elliptic curve cryptography. | Believed to be resistant to quantum attacks, as they are based on collision-resistant hash functions. |
| Mathematical Foundations | Primarily based on elliptic curve pairings and polynomial commitments. | Based on hash functions and information-theoretic principles (FRI protocol). |
| Primary Use Cases | Widely used in privacy-focused cryptocurrencies (e.g., Zcash) and blockchain scaling solutions (e.g., zk-Rollups). | Gaining traction in large-scale blockchain applications and systems where transparency and future-proofing are paramount. |
Data synthesized from.
2.4 The Practical Implications: Data Minimization and Shifting the Trust Model
The practical power of Zero-Knowledge Proofs lies in their ability to fundamentally reshape how trust and privacy are managed in digital systems. By enabling verification without disclosure, ZKPs provide the technical mechanism to enforce the principle of data minimization in a way that was previously impossible. Instead of a user having to share their entire driver’s license to prove they are over 18, a ZKP allows them to share only the cryptographic proof of that specific fact. This drastically reduces the amount of personal data that is shared, transmitted, and stored by service providers, thereby shrinking the “attack surface” available to malicious actors. This capability is critical for complying with modern data protection regulations like Europe’s GDPR, which mandate that only necessary data be collected—a principle that is present in spirit but lacks strong enforcement in Nepal’s current legal framework.
More profoundly, ZKPs facilitate a shift in the underlying trust model of digital interactions. The current model is based on trusting institutions—banks, government agencies, tech companies—to act as central authorities that hold and protect our data. This model has repeatedly proven to be flawed, as these centralized institutions can be hacked, coerced, or act negligently. ZKPs offer an alternative model where trust is placed not in fallible institutions, but in the verifiable and universally consistent laws of mathematics. A mathematically sound proof is valid regardless of who presents it or who verifies it, removing the need for a trusted intermediary. This shift from institutional trust to verifiable computation is the cornerstone of building more secure, private, and equitable digital systems for the future.
3.0 The Nepalese Digital Ecosystem: A Landscape of Opportunity and Vulnerability
3.1 E-Governance and the National ID (NID) Initiative: The Centralization Dilemma
Nepal’s National Identity (NID) card initiative, known as the Rastriya Parichaya Patra, stands as one of the country’s most ambitious digital governance projects. It is designed to be a federal-level, digital smart card that serves as the primary proof of identity for all citizens aged 16 and above. Each card contains a unique National Identity Number (NIN) and an embedded chip that securely stores a wealth of personal data, including demographic details (name, address, date of birth) and sensitive biometric information such as fingerprints of both hands and a digital photograph, with provisions for iris scans in some locations.
The intended purpose of the NID is to create a unified identification system that streamlines public service delivery. It is slated to eventually replace the traditional paper-based citizenship certificate and serve multiple functions, including as a voter ID card for elections and as the primary Know Your Customer (KYC) document for opening bank accounts, applying for passports, and accessing social security benefits. The rollout began in 2018 and has been expanding across all 77 districts, signaling a firm government commitment to this centralized digital identity model.
However, the architectural design of the NID system presents a profound vulnerability. By consolidating the most sensitive personal and biometric data of every citizen into a centralized government database, the system creates an extraordinarily high-value target—a digital “honeypot”—for sophisticated cyberattacks. This concentration of risk is particularly alarming in the context of Nepal’s documented cybersecurity weaknesses. The nation has already experienced significant breaches of government websites and critical infrastructure, demonstrating that its defenses are porous. The NID project, intended to be a cornerstone of modern governance, could inadvertently become the nation’s single greatest point of failure for information security if its underlying verification model is not re-architected to prioritize privacy and data minimization.
3.2 The Fintech Revolution: Growth Outpacing Security
Parallel to the government’s e-governance push, Nepal has experienced a vibrant and rapid expansion of its digital finance sector. This fintech revolution is led by the widespread adoption of digital wallets, with platforms like eSewa and Khalti by IME achieving market dominance. These services have evolved beyond simple payment gateways into comprehensive “lifestyle platforms,” enabling users to pay utility bills, book travel, purchase goods, and transfer funds with ease. With merchant networks numbering in the hundreds of thousands and a surge in the use of QR code payments, Nepal is making tangible progress toward the Nepal Rastra Bank’s vision of a cashless economy.
Despite this impressive growth, the security and privacy model of this ecosystem has not kept pace. These financial systems operate on a traditional, centralized architecture where users must entrust the service provider with extensive personal and financial data. This information is then stored in company-controlled databases, which have been proven vulnerable to attack in Nepal. The data breaches at major consumer-facing companies like Foodmandu (affecting over 50,000 users) and the internet service provider Vianet (leaking data of 170,000 customers) serve as stark warnings that such centralized data stores are prime targets for cybercriminals. While leading digital wallets employ security measures like bank-grade encryption and two-factor authentication (2FA), these protections primarily secure data in transit and at the point of login. They do little to mitigate the risk of a large-scale breach at the server level or prevent the potential for data misuse by the companies themselves, highlighting a fundamental flaw in the trust model.
3.3 The Cybersecurity Deficit: A Nation Underprepared
Nepal’s rapid digitalization is occurring against a backdrop of a significant national cybersecurity deficit.
The country’s legal and institutional frameworks are struggling to keep up with the evolving threat landscape. The primary piece of cyber legislation, the Electronic Transaction Act of 2008, is widely considered outdated and insufficient to address modern cybercrimes such as sophisticated ransomware attacks or state-sponsored espionage. Efforts to update this framework, such as the proposed Information Technology and Cyber Security Bill 2024, are steps in the right direction but have been slow to materialize and face challenges, including the continued absence of a dedicated national cybersecurity authority to centralize and coordinate defense efforts.
This institutional weakness is reflected in Nepal’s global standing; the country ranked 94th out of 182 nations in the 2020 Global Cybersecurity Index, indicating significant room for improvement. The threat is not theoretical. Cybercrime reports have risen dramatically, with incidents of social engineering, phishing, and online fraud becoming commonplace, suggesting a low level of cybersecurity awareness among the general public. This problem is critically exacerbated by a severe human resource deficit. Projections indicate a shortage of over 5,000 cybersecurity experts in Nepal by the end of 2024. The educational pipeline is failing to fill this gap, with university programs often criticized for being overly theoretical and lacking the practical, hands-on training required to produce industry-ready professionals capable of defending against modern threats.
3.4 The Data Privacy Paradox: Constitutional Rights Without Enforcement
Nepal’s digital landscape is characterized by a significant paradox: the legal recognition of privacy as a fundamental right coexists with a near-total lack of effective enforcement. Article 28 of the Constitution of Nepal 2015 explicitly guarantees the right to privacy for every citizen. This constitutional mandate is supported by statutes such as the Individual Privacy Act of 2018, which includes provisions on data collection, storage, and the requirement for individual consent.
However, this legal framework is a paper tiger. The most critical component of a functional data protection regime—an independent and empowered data protection authority—is absent in Nepal. Without such a body, there is no entity to proactively monitor compliance, investigate breaches, or impose meaningful penalties on violators. The existing laws are vague, failing to clearly define the specific responsibilities of data controllers and processors, provide clear rules for cross-border data transfers, or mandate public notification in the event of a data breach. This enforcement vacuum leaves citizens’ data highly exposed to misuse by both private companies and government agencies, while creating significant legal uncertainty for businesses attempting to operate in Nepal’s digital economy.
3.5 The Blockchain/Crypto Conundrum: Regulatory Fear Stifling Innovation
The regulatory environment surrounding blockchain and related cryptographic technologies in Nepal is defined by a single, overarching policy: a complete and strictly enforced ban on all cryptocurrency activities. The Nepal Rastra Bank (NRB), the nation’s central bank, has declared that any engagement in the trading, mining, or use of cryptocurrencies is illegal, citing the Foreign Exchange (Regulation) Act of 1962. This prohibition is actively enforced by multiple state agencies, including the Cyber Bureau of Nepal Police.
While this policy is aimed at preventing capital flight, money laundering, and financial instability, it has had a significant and detrimental side effect. The government’s hardline stance against speculative crypto-assets has created a chilling effect that stifles innovation and exploration of the underlying blockchain and cryptographic technologies, including Zero-Knowledge Proofs. Policymakers and the public often conflate the foundational technology with its most controversial application. This creates a significant psychological and regulatory barrier to proposing or implementing solutions that leverage these powerful tools for public good, even when they have no connection to creating or trading a currency. This “crypto conundrum” means that Nepal risks falling behind in the adoption of next-generation security technologies due to a regulatory posture that fails to distinguish between speculative financial instruments and transformative cryptographic protocols.
The confluence of these factors—the centralization of sensitive data in the NID system, the rapid but insecure growth of fintech, a weak national cybersecurity posture, an unenforceable privacy framework, and a regulatory aversion to advanced cryptography—has created a perfect storm of systemic risk. The current trajectory of Nepal’s digital transformation is not merely adding new services; it is concentrating risk on an unprecedented scale. Without a fundamental shift in the security model from one that futilely attempts to protect ever-larger centralized databases to one that prevents data over-sharing at the point of every transaction, a catastrophic, nation-scale data breach is not a matter of if, but when.
4.0 High-Impact ZKP Use Cases for Securing Nepal’s Information Infrastructure
The systemic vulnerabilities inherent in Nepal’s digital ecosystem necessitate a move beyond traditional security measures. Zero-Knowledge Proofs offer a suite of solutions uniquely capable of addressing these challenges at their core by enabling verification without data disclosure. The following use cases are not merely theoretical possibilities; they represent concrete, actionable applications tailored to mitigate the specific risks identified in Nepal’s national identity, financial, and e-governance sectors.
4.1 Use Case 1: Fortifying the National Digital Identity (NID) System
The NID system, as the intended foundational layer for all digital services, represents the single most critical point of intervention. Re-architecting its verification model with ZKPs would create a cascade of security and privacy benefits across the entire digital economy. This approach transforms the NID from a potential liability into a powerful, privacy-preserving asset for the nation.
4.1.1 Selective Attribute Disclosure
The Problem: The current model for using the NID card for verification—whether for opening a bank account, purchasing a SIM card, or accessing a government service—involves showing the physical card or a digital copy. This practice results in the massive over-sharing of sensitive personal information. A bar needs to verify a patron’s age, not their name, address, and unique NIN. A government office may need to confirm citizenship, not the individual’s date of birth. Each instance of over-sharing multiplies the risk of data misuse and identity theft.
The ZKP Solution: A ZKP-enabled system allows for selective attribute disclosure. A citizen would hold their NID credentials in a secure digital wallet on their smartphone. When a service provider requires verification, the user’s wallet, not the user, would generate a cryptographic proof for only the specific attribute required. For instance, it could generate a mathematically verifiable proof of the statement “the holder of this credential is over the age of 18” without revealing the birthdate. Similarly, it could prove “the holder is a resident of Bagmati Province” without disclosing their full address. This aligns with the principles of Self-Sovereign Identity (SSI), where the individual maintains control over their personal data and only discloses what is absolutely necessary for a given transaction.
4.1.2 Privacy-Preserving KYC/AML for Financial Institutions
The Problem: Current Know Your Customer (KYC) and Anti-Money Laundering (AML) processes in Nepal’s financial sector are data-intensive and insecure. Banks and financial institutions are required to collect and store physical or digital copies of identity documents like the NID card. These stored copies create vast, distributed repositories of sensitive citizen data, making each bank branch a potential target for data theft and placing a heavy compliance burden on the institutions themselves.
The ZKP Solution: ZKPs can revolutionize the KYC process. Instead of collecting and storing the NID, a bank’s system would request a ZKP from the prospective customer’s digital wallet. This proof would cryptographically verify several statements simultaneously, such as: “this individual possesses a valid, non-revoked NID issued by the Government of Nepal,” and “the biometric data of the person present matches the data cryptographically bound to this NID credential.” The bank receives absolute assurance of the customer’s identity and the authenticity of their credential without ever needing to see, handle, or store the underlying NIN, biometric data, or other personal details. This drastically reduces the risk of data breaches at financial institutions and streamlines the onboarding process.
4.1.3 Secure Biometric Authentication without Centralized Data Exposure
The Problem: The NID system relies on biometrics (fingerprints, photos) for definitive identification. Traditional biometric verification involves capturing a user’s live biometric data (e.g., a fingerprint scan at a terminal) and transmitting it over a network to a central server, where it is compared against a stored database. This process exposes the raw biometric data—an immutable and highly personal identifier—to interception during transit and to theft from the central database.
The ZKP Solution: ZKPs can enable biometric verification where the raw data never leaves the user’s personal device. The user’s NID credential, containing their encrypted biometric template, would be stored in their secure digital wallet. To authenticate, the user would provide a live biometric scan (e.g., to their phone’s sensor).
The wallet application would then generate a ZKP proving that the live scan matches the template stored within the credential. This proof, not the biometric data itself, is sent to the verifier’s system. The verifier is assured of the user’s identity without ever accessing the sensitive biometric information, effectively eliminating the risk of its theft or misuse.
Use Case 2: Enhancing Trust and Privacy in Digital Financial Services
Beyond identity verification, ZKPs can introduce new levels of privacy and security to a range of financial transactions, fostering greater trust in Nepal’s rapidly growing fintech ecosystem.
Verifiable Creditworthiness
The Problem: Applying for a loan or credit in Nepal requires individuals to submit extensive documentation of their financial history, including bank statements, salary slips, and transaction records. This process is not only cumbersome but also exposes a complete financial profile to the lending institution, creating significant privacy concerns.
The ZKP Solution: ZKPs allow for verifiable claims on private data. A loan applicant could authorize their bank’s application to interact with their financial data and generate ZKPs for specific claims required by the lender. For example, the applicant could prove that their “average monthly income over the last six months is above NPR 50,000” or that their “debt-to-income ratio is below 40%” without revealing the exact salary figures, individual transactions, or account balances. The lender receives the cryptographic assurance they need to make a credit decision, while the applicant’s detailed financial privacy is preserved.
Confidential Audits and Proof of Solvency
The Problem: Regulatory audits of banks and financial institutions are essential for ensuring the stability of the financial system. However, these audits often require regulators to access sensitive customer data, including account balances and transaction histories, which can create privacy risks and expose proprietary business information.
The ZKP Solution: Financial institutions can leverage ZKPs to prove compliance to regulators without revealing underlying confidential data. For example, a bank could generate a ZKP to prove that its “total assets meet the regulatory solvency requirements” or that “no single transaction in a given period exceeded the AML reporting threshold.” The Nepal Rastra Bank would be able to verify these proofs and confirm compliance without needing to inspect individual customer accounts, thus preserving client confidentiality while upholding strong regulatory oversight.
Use Case 3: Securing E-Governance and Public Service Delivery
ZKPs can be applied to some of the most sensitive areas of government-citizen interaction, ensuring that efficiency and accessibility do not come at the expense of privacy and integrity.
Architecting an Anonymous and Verifiable E-Voting System
The Problem: Digital voting systems face a fundamental conflict between two critical requirements: ensuring that each vote is cast by an eligible voter who has not voted previously (integrity) and ensuring that no one can link a voter to their specific vote (privacy). Traditional systems often struggle to guarantee both simultaneously, making them vulnerable to coercion, vote-selling, and manipulation.
The ZKP Solution: ZKPs provide a powerful cryptographic toolkit to resolve this conflict. A ZKP-based e-voting system could work as follows: A voter uses their NID digital wallet to generate a ZKP that proves they are on the official electoral roll and have not yet cast a ballot. This proof is submitted to receive a unique, anonymous voting token. The voter then casts their ballot, which is cryptographically linked to the anonymous token, not their identity. The system can publicly count the valid tokens to ensure the tally is correct, while the ZKP mechanism makes it mathematically impossible to trace a ballot back to the individual voter who cast it. This approach provides strong guarantees of both election integrity and voter privacy.
Enabling a Secure and Private Health Information Exchange (HIE)
The Problem: Sharing patient health information between different hospitals, clinics, and insurance providers is crucial for effective care but is fraught with immense privacy risks. Patients are often reluctant to have their complete medical history digitized and shared, fearing stigma, discrimination, or unauthorized access. Nepal’s current legal framework lacks specific, robust protections for health data akin to international standards like HIPAA.
The ZKP Solution: A ZKP-based Health Information Exchange would empower patients with granular control over their medical data. A patient could use a health wallet to generate proofs for specific medical facts when needed. For instance, when visiting a new specialist, they could provide a ZKP for the statement “I have a diagnosed allergy to penicillin” or “my insurance policy with XYZ provider is currently active” without having to share their entire electronic health record. Researchers could also use ZKPs to verify that participants in a clinical trial meet certain criteria (e.g., “age between 40-50,” “not a smoker”) without accessing their personal identities, facilitating vital medical research while upholding the highest ethical standards of patient confidentiality.
A Strategic Roadmap for ZKP Adoption in Nepal
The successful integration of Zero-Knowledge Proofs into Nepal’s digital fabric requires a deliberate, phased, and pragmatic strategy. It must directly address the nation’s unique challenges related to infrastructure, human capital, and the regulatory environment. This roadmap outlines a multi-year approach designed to build foundational capacity, demonstrate value through targeted pilots, and scale toward ubiquitous, nation-wide adoption.
Overcoming Implementation Barriers: A Pragmatic Approach
A successful strategy must begin by acknowledging and planning for the primary obstacles to adopting advanced cryptographic technologies in the Nepalese context.
Infrastructure Deficit
The computational intensity of generating ZKPs can be a significant hurdle, especially for citizens with low-powered mobile devices or in areas with unreliable connectivity. The significant digital divide between urban and rural areas in Nepal, characterized by disparities in internet access and electricity, must be a central consideration. To mitigate this, the initial rollout should focus on architectures that minimize the burden on the end-user. This includes prioritizing Non-Interactive ZKPs (NIZKs), which do not require real-time communication, and designing systems that can leverage server-side or third-party prover services for computationally heavy tasks. Furthermore, applications must be engineered to function effectively in low-bandwidth environments, ensuring that rural and remote populations are not excluded from the benefits of secure digital services.
Skills Gap
Nepal faces a critical shortage of professionals with expertise in advanced cybersecurity and applied cryptography. A purely domestic effort to build ZKP-based systems is currently unfeasible. The solution must be two-pronged. In the short term, Nepal should actively seek partnerships with international technology firms and cryptographic experts for the initial system design, architecture, and crucial knowledge transfer. In parallel, a long-term national education strategy must be launched. This involves a comprehensive update of university curricula for computer science and IT programs, moving beyond foundational theory to include practical, hands-on training in modern cryptography, ZKP development languages and frameworks (e.g., Noir, Circom, Cairo), and specialized fields like ethical hacking and secure systems design.
Policy and Legal Framework
The current legal landscape is inadequate to support a ZKP-based ecosystem. The proposed Information Technology and Cyber Security Bill provides a timely opportunity for reform. It is imperative that this bill be amended to explicitly recognize cryptographically generated proofs as a legally valid means of verification for identity and other attributes. This would provide the legal certainty required for both public and private sector adoption. Crucially, the new legal framework must mandate the establishment of a well-resourced and independent Data Protection Authority, empowered to enforce data minimization principles and oversee the implementation of privacy-enhancing technologies.
Regulatory Mindset (The Crypto Hangover)
The blanket ban on cryptocurrencies by the Nepal Rastra Bank has created a significant psychological and regulatory barrier, as ZKPs and blockchain are often incorrectly conflated with speculative assets. Overcoming this “crypto hangover” is a prerequisite for any progress. This requires a deliberate and sustained communication strategy aimed at educating policymakers and regulators. The focus must be on de-linking the foundational security technology of ZKPs from the financial application of cryptocurrencies. A key mechanism to achieve this is the creation of a “regulatory sandbox”. This would be a controlled environment, overseen by the NRB and the Ministry of Communications and Information Technology, where banks, fintech companies, and government agencies can experiment with ZKP-based solutions for non-currency applications like KYC and identity verification.
This hands-on, low-risk approach would allow regulators to observe the benefits of the technology directly, build trust, and develop informed, nuanced policies that foster innovation while managing risk.
5.2 A Phased Implementation Approach: From Pilot to Nation-Scale
A gradual, evidence-based rollout will build momentum, demonstrate value, and allow for iterative learning and adaptation.
Phase 1 (12-24 Months): Foundational Pilots and Capacity Building
The initial phase focuses on demonstrating the viability and benefits of ZKPs through small-scale, high-impact pilot projects while simultaneously building the necessary human and institutional capacity.
- Pilot Project 1: ZKP-Based Age Verification. A collaboration between the Department of National ID and Civil Registration (DoNIDCR) and a major telecommunications provider to implement a ZKP-based age verification system for purchasing a new SIM card. This is a well-defined, low-risk use case that clearly demonstrates the principle of selective disclosure and provides a tangible public benefit.
- Pilot Project 2: ZKP-Based Proof of Balance. A partnership between a leading commercial bank and a major digital wallet (e.g., eSewa or Khalti) to pilot a system where users can prove they have sufficient funds for a specific merchant payment without revealing their actual account balance. This would showcase the technology’s application in enhancing privacy in everyday financial transactions.
- Key Actions:
- Establish a national multi-stakeholder Task Force on Privacy-Enhancing Technologies (PETs), comprising representatives from government, the NRB, the private sector, and academia.
- Launch the cybersecurity and cryptography upskilling programs outlined in section 5.1.
- Begin drafting the necessary amendments to the IT and privacy laws.
Phase 2 (2-4 Years): Scaling and Integration
Building on the success of the pilot projects, this phase focuses on developing standardized infrastructure and expanding the application of ZKPs to core sectors.
- National Digital Identity Wallet Standard: The PETs Task Force will develop and publish a national standard for a secure “Digital Identity Wallet.” This wallet will be designed to securely store NID credentials and have the capability to generate and manage ZKPs, ensuring interoperability across different government and private sector services.
- Integration into the Banking Sector: Begin the formal integration of ZKP-based KYC processes, starting with a cohort of major commercial banks. This will involve updating the NRB’s KYC directives to recognize ZKP verification as a compliant method.
- E-Voting Proof-of-Concept: The Election Commission, in collaboration with technical partners, will develop a comprehensive proof-of-concept for a ZKP-based electronic voting system to be tested in mock or non-binding elections.
Phase 3 (5+ Years): Ubiquitous Adoption and Advanced Use Cases
In the final phase, ZKPs transition from a niche technology to a foundational component of Nepal’s digital infrastructure.
- Mandatory ZKP Verification: The government mandates that all new citizen-facing digital services must use the national Digital Identity Wallet and ZKP-based verification for authentication and attribute checks.
- Advanced Use Case Rollout: Launch the more complex, large-scale ZKP applications, such as the national Health Information Exchange (HIE) and the use of ZKPs for confidential regulatory audits across the financial sector.
- International Leadership: With a mature and functioning privacy-preserving digital ecosystem, Nepal can position itself as a regional leader in digital governance, attracting investment and talent in the high-tech sector.
5.3 Fostering a ZKP-Ready Ecosystem: The Power of Collaboration
No single entity can drive this transformation alone. Success is contingent on building a robust ecosystem through strategic partnerships.
- Public-Private Partnerships (PPPs): Strong, formalized collaborations are essential between government bodies like the Ministry of IT and DoNIDCR, private sector leaders in banking and fintech, and the nation’s universities. The private sector can provide the agility and technical expertise for implementation, while the government provides the legal framework, standards, and authoritative identity source (the NID).
- International Collaboration: Nepal should not develop these systems in a vacuum. It is crucial to learn from the successes and failures of international models, such as Estonia’s advanced e-governance system, India’s experience with Aadhaar and its privacy challenges, and British Columbia’s pioneering use of anonymous credentials for public services. Engaging with global standards bodies and seeking technical assistance from international development partners can accelerate progress and ensure that Nepal’s solutions are built on world-class foundations.
6.0 Conclusion and Strategic Recommendations
6.1 The Strategic Choice for Nepal: From Data Vulnerability to Digital Sovereignty
Nepal stands at a critical juncture in its digital evolution. The current trajectory—characterized by the rapid centralization of citizen data into systems protected by an underdeveloped cybersecurity apparatus and an inadequate legal framework—is not sustainable. It is a path that leads toward an inevitable, large-scale information security crisis that could erode citizen trust, cripple the economy, and compromise national security. The continued reliance on a model of institutional trust in an era of trustless technology is a strategic miscalculation.
This report has demonstrated that an alternative path is not only possible but necessary. The adoption of Zero-Knowledge Proofs offers a fundamental re-architecting of Nepal’s digital infrastructure, shifting the paradigm from data accumulation to data minimization, and from institutional trust to cryptographic verifiability. This is more than a technological choice; it is a strategic decision to build a digital future that is resilient, secure, and respectful of the fundamental rights of its citizens. By embracing ZKPs, Nepal can transform its digital vulnerabilities into a source of strength, creating a trustworthy ecosystem that fosters innovation and safeguards its digital sovereignty in an increasingly complex world.
6.2 Consolidated Strategic Recommendations
To translate this vision into reality, a coordinated and decisive effort is required from all key stakeholders. The following recommendations are prioritized to create maximum impact and build sustainable momentum.
For the Government of Nepal (Cabinet & Parliament):
- Prioritize ZKP Integration into the NID System: Immediately commission a comprehensive feasibility study and technical architecture plan for a ZKP-enabled National Digital Identity wallet. This initiative should be designated a matter of national security priority, recognizing that the security of the NID underpins the entire digital economy.
- Modernize the Legal Framework: Urgently advance and pass the Information Technology and Cyber Security Bill, with critical amendments to: (a) explicitly grant legal recognition to cryptographic proofs as a valid method for identity and attribute verification, and (b) mandate the establishment of an independent, fully-empowered Data Protection Authority to enforce privacy laws.
- Launch a National Digital Literacy and Cybersecurity Upskilling Program: Authorize and fund a multi-year national initiative, in partnership with educational institutions and the private sector, focused on building a domestic talent pool in applied cryptography, secure software development, and advanced cybersecurity defense.
For Nepal Rastra Bank (NRB):
- Establish a Fintech Regulatory Sandbox: Create a formal “safe harbor” program to allow financial institutions and fintech companies to pilot ZKP-based solutions for KYC, credit scoring, and secure payments. This program’s charter must explicitly de-link the evaluation of these privacy-enhancing technologies from the existing ban on cryptocurrencies to foster responsible innovation.
- Develop a Standard for Privacy-Preserving Financial Audits: Initiate a working group with commercial banks and auditing firms to create a framework for using ZKPs to conduct regulatory compliance checks and solvency audits, establishing a new national standard that enhances oversight while protecting customer data confidentiality.
For the Private Sector (Banks, Fintechs, Tech Companies):
- Form a Public-Private Consortium for ZKP Standards: Proactively collaborate to establish a consortium dedicated to developing open, interoperable standards for ZKP-based identity and data verification. This will prevent the creation of fragmented, proprietary systems and ensure a seamless user experience across the digital ecosystem.
- Invest in Research and Development: Forge strategic partnerships with Nepal’s leading universities to create local research and development hubs. These hubs should focus on applied research, adapting and optimizing ZKP technology to solve challenges specific to the Nepalese context, thereby building local expertise and intellectual property.


